Are you Cybersecurity Manager in Aviation?
A Cybersecurity Manager working in the Aviation sector also needs to know about AVSEC (Aviation Security).
It is within their remit, and it’s also defined in their organizations’ security manual. You can outsource it – but the Cybersecurity Manager still retains full responsibility. Which might comes as a surprise to a lot of you.
Are you a Cybersecurity Manager working for a regulated entity in accordance with your country’s NCASP?
Wait, you don’t know what a regulated entity is? Or what the NCASP is?
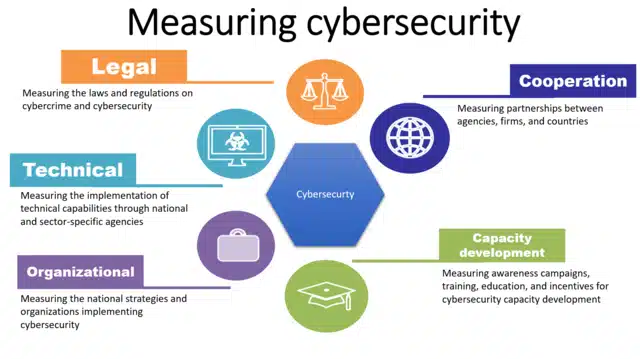
Under the NCASP (National Civil Aviation Security Plan) Security Managers are legally responsible for their own organization’s obligations. Let me repeat that – if you are a Security Manager then YOU ARE LEGALLY RESPONSIBLE for failing to comply with the obligations of your company in matters of security. Malicious activities such as breaches or attacks are yours to answer for.
The NCASP (National Civil Aviation Security Program) is derived from EU regulations that come from ICAO guidelines. The NCASP is the document created by your national authority that tells you how to do your job as Cybersecurity manager as it relates to Aviation Security. Or AVSEC as we call it.
What is Critical Infrastructure?
Regulated entities are anyone that operates at the Airport, delivers, or serves the airport/airline community, or delivers products or services into the SRA (Security Restricted Area). This includes Airlines, Airports, Handling Agents, Fuellers, Air Traffic Controllers, or anyone that works at the Airport. So, everybody, everywhere.
And this regulatory framework – and the NCASP – includes Cybersecurity strategy.
Cybersecurity within Aviation
Security is not Safety.
They are separate and different. You have safety protocols such as systems, training, and safety management protocols but you also have Security. With identical types of protocols but dealing specifically with security and devices. Each entity (company) operating under the NCASP must have a Security Manager.

He or she works with a Security Program that outlines all the steps they take to stop attackers or threats in day-to-day operations. CHAPTERS in the NCASP deal with the regulations (read: obligations) of each area. How you protect your company from attacks, how you train staff and how to do background checks on people who join your organization. This is the responsibility of the Cybersecurity Manager.
Chapter 15 of the NCASP
Is Cybersecurity. So, the responsibility for Cyber activity is at the doorstep of the Security Manager. Not only that, but the efforts and strategy around Cyber threats must be contained in the security program.
We know a lot about the Avsec landscape, and we have been looking closely at this topic for a couple of years. Cybersecurity has been around for a while and malicious software has caused issues for Airlines. And this will continue at pace until the end of time.
Cyber attackers are constantly using ransomware to attack poorly defended, out of date devices. But while the NCASP is good at the practical stuff of hiring staff or putting up fences, we have been slow on the approach to Cybersecurity. Most worryingly, the Security Manager of the regulated entity is rarely a trained Cybersecurity whizz kid.
Cloud Cybersecurity
In a lot of cases Security Managers are just trying to run a business and trying to stop stuff from being tampered with or stolen. Most companies do have IT software systems and IT cloud services that are run by the IT department. But these can be separate from normal Avsec operations.
And herein lies the problem. In recent years, some big airlines have started to see the need to create “pods” or teams that are handling these issues to ensure the protection of systems. But these cybersecurity controls are the exception.
Cyber Security Regulations
The core Cybersecurity regulations cover what we deem CRITICAL INFRASTRUCTURAL SYSTEMS.
Here they are
- Aircraft
- ATC (Air Traffic Control)
- Data Protection (Passengers, Staff, Cargo)
- Networks

As you can see these are the core elements of Aviation. Where critical software executes an enormous amount of work, and any cybersecurity incident could be extremely dangerous. As you can imagine the IT security around Aircraft communications systems, Air Traffic Control systems, and Airport data centers are well protected.
With layers of cyber security as well as multiple backup systems. But as the world becomes increasingly digital – and we use devices to share data and use APIs to make the passenger journey sleeker and more fluid. We open the door for those who wish to do us harm.
Attacks
“Known and Unknown threats” to use a popular phrase. Here are the primary threats to Civil Aviation.
- Religious Fanatics
- Criminals
- Political activists
- Mental Health sufferers and substance abusers
There are also Insider Threats. Where staff can abuse their position (or attain it purposefully) to commit an act. Like stealing an aircraft to take it for a joy ride.
Who are Cyber Attackers targeting?
In most cases – you. That’s right. The easiest and most effective way to beat Cybersecurity is to gain access. Just as an employee would via login credentials or direct hard access, such as popping in a USB key. The most professional and diligent Cyber Security software team can be beaten by a low-level employee that just walks into a server room and sticks a USB stick into a server.
Similarly, a check-in desk staff member that leaves her post for a few minutes can allow a bad actor to access a system with millions of people’s flight and personal information. A phishing email or a trojan virus, targeted at the right person can also allow access to systems that can threaten flights.

Cybersecurity Manager Response
Hire the right people. Since 2019, the background checking parameters have changed dramatically. In days of yore, we would call up 1 or 2 previous employers and you were good to go. Now, thankfully, it’s a different ball game.
Your criminal history is checked via your local law enforcement, as are your social media and other online postings. They also check regional and sometimes global intelligence data sources. And they do this for up to 5 years prior and in all the countries you have lived to that point.
Mobile Devices
If you’ve been political on some social media sites, then you can expect this to be flagged if you apply for an Airport ID or apply to be a security manager at a regulated entity. But this shouldn’t come as a surprise. If you are planning to enter the United States sometime in the future, this is part of their checking process. There’s a rule that we stick by here at WT towers – don’t say anything on social media that you wouldn’t mind being posted on the front page of tomorrow’s Wall Street Journal.
Other than that, your company should really be doing a lot of training for staff. All staff that have any access to online systems could be threatened by Cybercrime. This training should include (as a minimum) how to deal with suspicious emails, social media hacks, phone or text hacks, and phishing simulators.
And what you want to focus on is reporting. Staff need to report anything they deem unusual to you immediately. The faster you spot something, the easier the remedy.
Cybersecurity Managers Avsec 101
A Cybersecurity Manager needs to be aware of the IT Cyber strategy because whether you like it or not, it is going to be part of your domain. Security is security whether the breaches are through a fence or door or via a password hack. Why? Because the target is the same. Passengers, baggage, infrastructure, or Aircraft are always the target.
Those guys trying to hack your IT are not after some other thing that doesn’t affect you. They are after the very same valuable stuff that you have, except they can do it from a great distance and anonymously. Or they can use you or your staff (knowingly or unknowingly) to do it for them. And if that sounds far-fetched then we can point to many examples of how vulnerable people can be tricked into doing unbelievable things if the perpetrator is willing to invest time and effort and is persistent.

As a Security Manager, we advise leaving the 1s and 0s to the IT experts but make sure you are compliant, and the systems are suitable for your operation. After that – hire and support staff so they are best equipped for these Cyber attacks.



